DORA
The aim of the DORA regulation (Digital Operational Resilience Act) is an EU-wide framework for the management of cybersecurity and ICT risks in the financial sector.
The aim of the DORA regulation (Digital Operational Resilience Act) is an EU-wide framework for the management of cybersecurity and ICT risks in the financial sector.


With the growing reliance on digital technologies, not only does the risk of cyberattacks increase, but the potential consequences of such attacks also become more severe. In addition, unintentional and non-malicious IT problems, such as software errors or system failures, also represent a significant risk in the digitalized financial world.
Existing regulations for financial actors, e.g. BAIT, VAIT, ZAIT, should be brought into line with the new DORA regulation.
Having supported our clients with compliance efforts, we know that efficiency is key for achieving your desired resilience posture while ensuring compliance with DORA requirements.

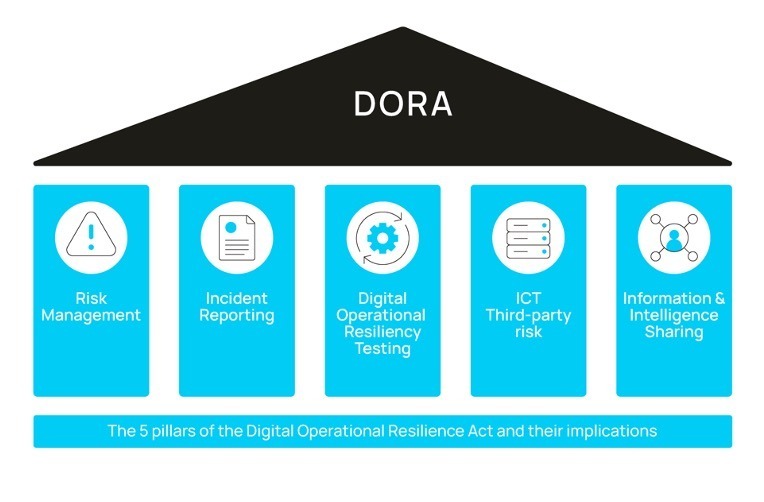
ICT risk management

Managing ICT third-party risk

Information and Intelligence Sharing

Management of ICT incident reporting and cyber security:

Digital operational resilience testing
